The shift from pure 'cost' focus to a focus on 'shared risk' and 'value' when engaging with your third parties.
Menu
Reduce risk from exposure to your third parties. Meet regulatory compliance.
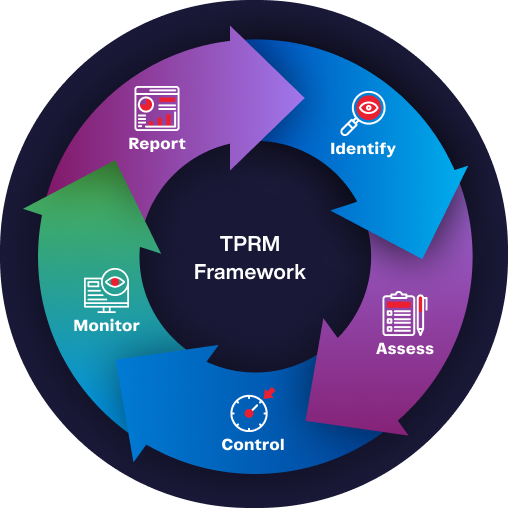
Fully Automated Third-Party Risk Management (TPRM) Lifecycle

Manage third party risk at the speed of business
We help provide a simple yet comprehensive enough solution for SMEs (Small and Medium Enterprises) who need an automated and cost-effective solution to manage their third-party vendors and supplier risks.
- Delivers readily accessible risk intelligence reports.
- Automated and enhanced vendor risk assessments.
- Elevate risk posture of your third parties.
- Achieve regulatory compliance with ease and avoid penalties.
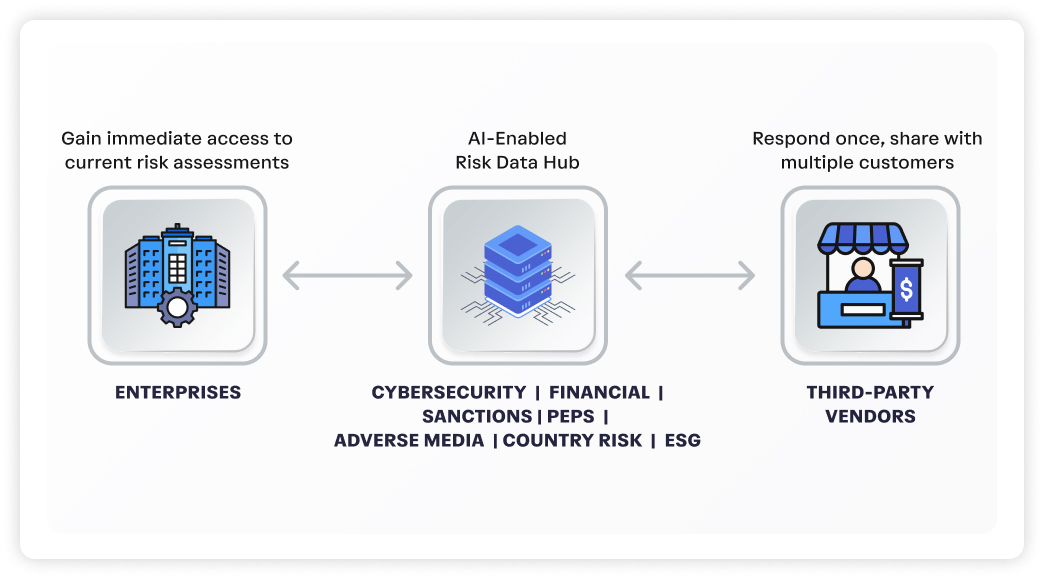
An automated third-party risk management solution that
benefits both enterprises and their third parties
Near real-time continuous monitoring
Building your vendor inventory is easy and fast with OPEN3PRX™.
- Easily search, find and add a third-party vendor from our extensive OPEN3PRX™ database automatically.
- Can’t find the vendor? Simply submit a request and the platform automatically onboards the vendor profile.
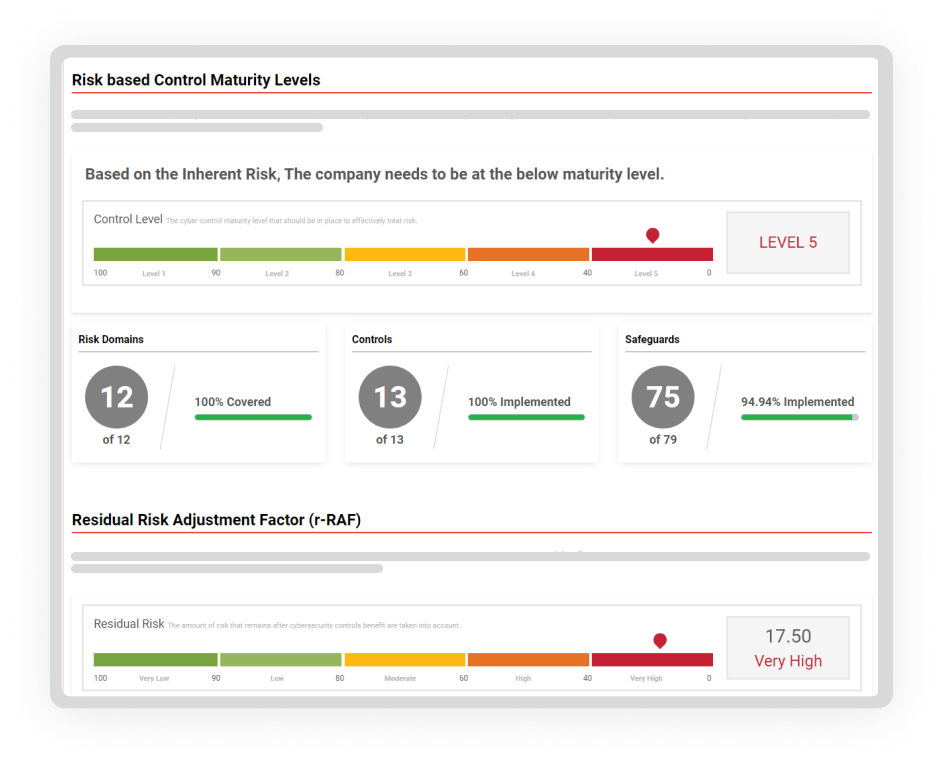
Risk identification is the process of determining risks that could potentially prevent an enterprise from achieving its objectives. Our vendor pre-assessment automatically recommends the control maturity level that should be in place to effectively treat risk, the inherent risk and the business impact.
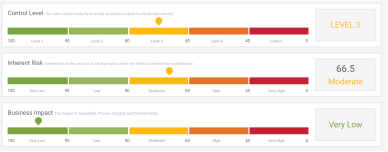
- Ability to determine the cyber control maturity level that should be in place to effectively treat risk.
- Ability to determine the Inherent risk.
- Ability to determine the Business Impact – Availability, Process Integrity, and Confidentiality.
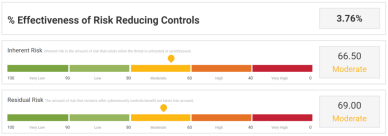
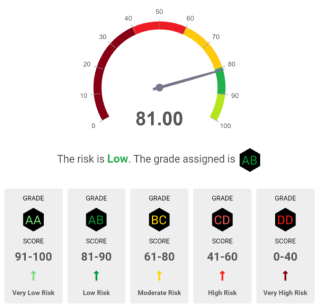
Risk Assessment is the process of assessing and analyzing identified risks. Leverage our industry standard OPEN3PRX™ TPRM framework that adopts an efficient risk-based approach in assessing third parties. Use one of our five TPRM levels (Level 1 for Very Low Risk vendors to Level 5 for Very High Risk vendors).
Your organization can also easily build your own custom assessments from our library.
- Ability to initiate risk assessments and send questionnaire to one or more third parties.
- Automated evaluation and calculation of residual risk score. The amount of risk that remains after controls benefit are considered.
- Automated initiation of recertification based on third-party risk categorization.
Risk Controls help mitigate or reduce the impact of a risk. Controls Audit / Assessment is the process of assessing and analyzing whether a third-party has adequate controls designed and properly implemented including the effectiveness of the controls. An improperly designed control or an ineffective control does not serve the purpose of mitigating risks. Thus, controls need to be tested periodically and certified by a competent risk controls expert.
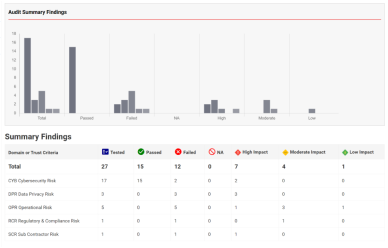
- Ability to perform internal and external audits of controls.
- Ability to generate controls audit summary.
Leverage our comprehensive automated risk intelligence engine that analyzes 100+ data elements to vet third parties.
Leverage our continuous monitoring capability on third parties globally across 195 countries. We cover business risks, cybersecurity, breaches, financial stability, commercial risk, credit risk, bankruptcy & legal issues, sanctions and fraud, PEP, adverse media, country risk, ESG related risks.
Ability to continuously monitor to receive smart alerts and trigger actions.
Organizations can integrate the following to monitor third-parties on a near real-time basis.
- Cybersecurity Ratings
- Financial Health Ratings
- Sanctions, PEP, Adverse Media Insights
- Country Risk
Ability to share reports to internal management and external auditors / examiners.
Some standard reports are listed below.

- Third Party Risk Intelligence Report
- Third Party Pre-Assessment Report
- Third-Party Risk Assessment Report
- Third-Party Cyber Maturity Report
OPEN3PRX™ risk framework covers all aspects of risks related to third parties
Risk Dimensions
0
Risk Categories
0
Risk Controls
0
CYB
technology RISK
DPR
compliance risk
RCR
financial health risk
FHR
operational risk
OPR
technology RISK
STR
strategic risk
SCR
sub-contractor risk
CON
concentration risk
GEO
geographical risk
REP
reputational risk
org organization Risk ESg
CON
Risk Categories
0
Risk ControlS
0
concentration
Concentration risk looks to see if you have all eggs in one basket. It covers vendor concentration across critical services, critical skills, geography
GEO
Risk Categories
0
Risk ControlS
0
geographic
Geographic risk covers specific country risk such as political, civil unrest, extreme weather, natural disasters, climate ,health etc
REP
Risk Categories
0
Risk ControlS
0
reputational
Reputational Risk covers good and bad press (Positive and Negative news) that includes lawsuits, brand defamation, management conduct and ethics
OSC
Risk Categories
0
Risk ControlS
0
operational & supply chain
Operational & Supply Chain covers Business continuity,Disaster recovery, Physical security, business resilience, performance management, human resources risks
STR
Risk Categories
0
Risk ControlS
0
strategic
Strategic risk covers risks related to M&A activities, overall alignment to outsourcing, service delivery risk, new market expansions etc
SCR
Risk Categories
0
Risk ControlS
0
sub-contractor
Sub-contractor risks covers all aspects of due-diligence related to 4th parties (sub-contractors) and theis sub-contractors (Nth parties)
DPR
Risk Categories
0
Risk ControlS
0
data & privacy
Data and Information Privacy covers the collection and dissemination of data in line with various privacy regulations
RCR
Risk Categories
0
Risk ControlS
0
regulatory & compliance
Regulatory and Compliance covers the ever-changing regulatory requirements and compliance.
FHV
Risk Categories
0
Risk ControlS
0
financial health
Financial Health covers the organizations ability to meet its financial obligations
ORG
Risk Categories
0
Risk ControlS
0
organizational
Organizational risks includes the business services, industry vertical, company legal & ownership structure, jurisdiction
ESG
Risk Categories
0
Risk ControlS
0
ENV.-social-governANCE
Environmental,Social, and Corporate Governance
(ESG) refers to the three central factors in
measuring the sustainability and societal impact
of a company or business.
CYB
Risk Categories
0
Risk ControlS
0
tech & cybersecurity
Technology & Cybersecurity covers all aspects of technical infrastructure, information security and cyber resilience
REP
Risk Categories
0
Risk ControlS
0
reputational
Reputational Risk covers good and bad press (Positive and Negative news) that includes lawsuits, brand defamation, management conduct and ethics
GEO
Risk Categories
0
Risk ControlS
0
geographic
Geographic risk covers specific country risk such as political, civil unrest, extreme weather, natural disasters, climate ,health etc
CON
Risk Categories
0
Risk ControlS
0
concentration
Concentration risk looks to see if you have all eggs in one basket. It covers vendor concentration across critical services, critical skills, geography
SCR
Risk Categories
0
Risk ControlS
0
sub-contractor
Sub-contractor risks covers all aspects of due-diligence related to 4th parties (sub-contractors) and theis sub-contractors (Nth parties)
STR
Risk Categories
0
Risk ControlS
0
strategic
Strategic risk covers risks related to M&A activities, overall alignment to outsourcing, service delivery risk, new market expansions etc
OSC
Risk Categories
0
Risk ControlS
0
operational & supply chain
Operational & Supply Chain covers Business continuity,Disaster recovery, Physical security, business resilience, performance management, human resources risks
FHR
Risk Categories
0
Risk ControlS
0
financial health
Financial Health covers the organizations ability to meet its financial obligations
RCR
Risk Categories
0
Risk ControlS
0
regulatory & compliance
Regulatory and Compliance covers the ever-changing regulatory requirements and compliance.
DPR
Risk Categories
0
Risk ControlS
0
DATA & PRIVACY
Data and Information Privacy covers the collection and dissemination of data in line with various privacy regulations
CYB
Risk Categories
0
Risk ControlS
0
tech & cybersecurity
Technology & Cybersecurity covers all aspects of technical infrastructure, information security and cyber resilience
ESG
Risk Categories
0
Risk ControlS
0
ENV.-social-governANCE
Environmental,Social, and Corporate Governance
(ESG) refers to the three central factors in
measuring the sustainability and societal impact
of a company or business.
ORG
Risk Categories
0
Risk ControlS
0
organizational
Organizational risks includes the business services, industry vertical, company legal & ownership structure, jurisdiction
Recent Articles
Third-party governance and risk management is emerging as a significant board level topic.
Leveraging Artificial Intelligence in Third Party Risk Management
Frequently Asked Questions
TPRM is the process of identifying, assessing, and mitigating the potential risks that third-party vendors or partners pose to an organization’s data, operations, and reputation.
With growing digital transformations, organizations are increasingly reliant on third parties exposing them to several risks such as cybersecurity, data privacy, financial, regulatory and more. Managing third-party risks helps protect sensitive data, maintain business continuity, and safeguard the organization’s reputation.
Third parties can introduce risks related to data breaches, compliance violations, financial instability, supply chain disruptions, and more.
Identification involves evaluating factors such as vendor access to sensitive data, the nature of the relationship, and the vendor’s security practices.
A risk assessment is the process of evaluating the likelihood and impact of potential risks posed by a third party. It helps prioritize and focus mitigation efforts.
Mitigation strategies may include contract terms, security audits, monitoring, and vendor education to ensure compliance with security and privacy standards.
The frequency of assessments depends on the nature of the relationship and the associated risks. High-risk vendors may require more frequent assessments.
Regulations like GDPR, HIPAA, and various industry-specific standards often mandate third-party risk management to protect sensitive information.
TPRM tools and software can streamline risk assessments, automate monitoring, and provide real-time insights into third-party performance and compliance.
Best practices include establishing a clear governance framework, conducting due diligence when onboarding vendors, regularly reviewing and updating risk assessments, and fostering collaboration between business and security teams.
Best practices include establishing a clear governance framework, conducting due diligence when onboarding vendors, regularly reviewing and updating risk assessments, and fostering collaboration between business and security teams.
Organizations should have an incident response plan in place to address breaches promptly. This may involve notifying affected parties, conducting a root cause analysis, and taking corrective actions.
TPRM programs should be flexible and regularly reviewed to incorporate new threats, regulations, and lessons learned from previous assessments.
Organizations can access industry standards, guidelines, and consult with experts or use TPRM software to streamline their processes.
A robust TPRM program demonstrates a commitment to security and compliance, enhancing an organization’s reputation and building trust with customers and
Challenges include resource constraints, the complexity of managing multiple vendors, and keeping up with evolving threat landscapes and regulations.