In an era where data security and privacy are paramount, businesses handling sensitive information
Sell more cyber insurance faster
- Effectively market and sell more Cyber Insurance 10x faster and grow top line.
- Automated online application, risk assessment. Easily integrate with your customer facing website.
- Electronically transmit ‘quote-ready’ applications to the insurance carrier or underwriter.
- Generate additional revenue stream by providing Risk Management solutions to your clients.
- Meet regulatory requirements related to Information and Cyber Security guidelines or regulation.
Sell More, Sell Fast
Smart Prospecting
How it works?
Easily build Portfolio from database
Generate KYC & Cyber Report
Initiate Intelligent Conversation
Offer Risk Mitigation Recommendations
Digitize Application Flow
Enhance Customer Experience
Streamline your processes with automated online applications and risk assessments, all customized with your own branding.
How it works?
Integrate Application Flow with your branding
Broker Website or Email Channel
Initial Application
Quick qualifier application to assess inherent risk
Automated Risk Based Underwriting Questionnaire
Detailed risk-based assessment
Transmit to Insurers
Risk Adjustment Factors & Cyber Maturity Report
Potential New Revenue
Improve Cyber Risk Posture of Insured
How it works?
Onboard customer with FREE subscription
A Risk & Compliance platform for your insured
Monitor Cyber Vulnerabilities
Perform periodic vulnerability assessments
Risk & Control Assessments
Guidance on Security and Risk Reducing Controls
Certifications & Compliance
Stay compliant with policies, controls and regulations
Stay Compliant
Regulatory Compliance
Stay ahead of the game, confidently navigating the regulatory guidelines related to cybersecurity, privacy and third-party risks, thus safeguarding your professional standing.
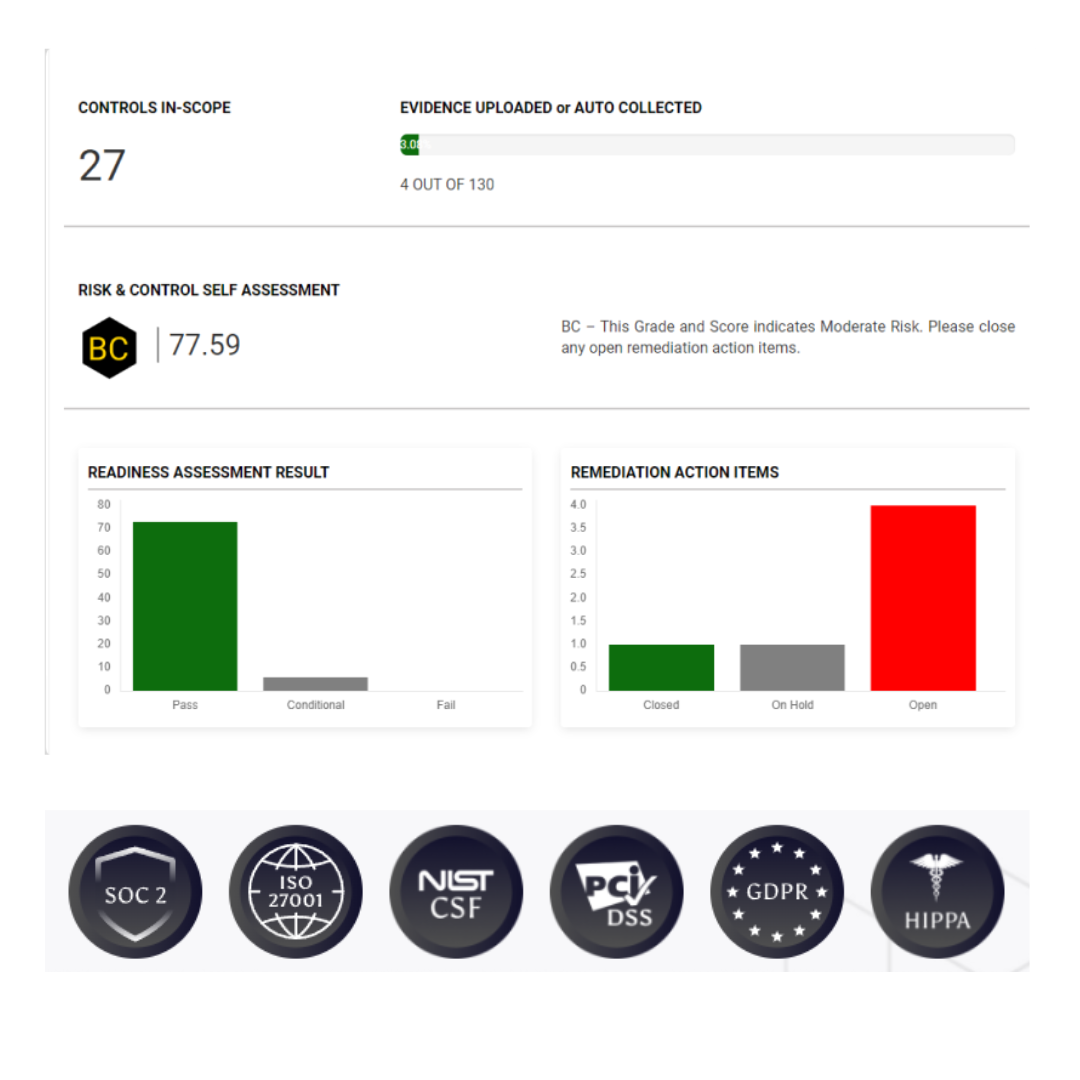
How it works?
Perform a Compliance Readiness
We provide an easy compliance checklist
Leverage our ready framework
All control requirements are readily available
Conduct an Internal Assessment & Audit
Leverage our risk assessment and audits module
Become Compliant
Stay Compliant year after year
ISO/IEC 27001 is the world’s best-known standard for information security management systems (ISMS).
In the rapidly evolving digital landscape, businesses face an unprecedented level of cyber threats,
- Legal and civil damages: Paying for legal representation and possible damages related to a privacy or network security breach;
- Security breach remediation and notification expenses: Notifying affected parties and mitigating potential harm from a privacy breach, such as providing free credit monitoring;
- Forensic investigations expenses: Hiring a firm to investigate the root cause and scope of the data breach;
- Computer program and electronic data restoration expenses: Restoring or recovering damaged or corrupted data caused by a breach, denial-of-service attack or ransomware.
- Data confidentiality breaches: The loss of and/or unauthorized access to or disclosure of confidential or personal information;
- Cyber extortion: A demand for payment under threat of causing harm to your data; for example, disabling your operations or compromising your confidential data;
- Technology disruptions: A technology failure or denial-of-service attack.
- How many records containing personal information does your organization retain or have access to?
- How many records containing sensitive commercial information does your organization retain or have access to?
- What security controls can you put in place to reduce the risk of having your system compromised?
- Do all portable media and computing devices need to be encrypted?
- Is unencrypted media in the care, custody or control of your third-party service providers?
- Could you make a claim if you were unable to detect an intrusion until several months or years had passed?




